Threats from wireless network
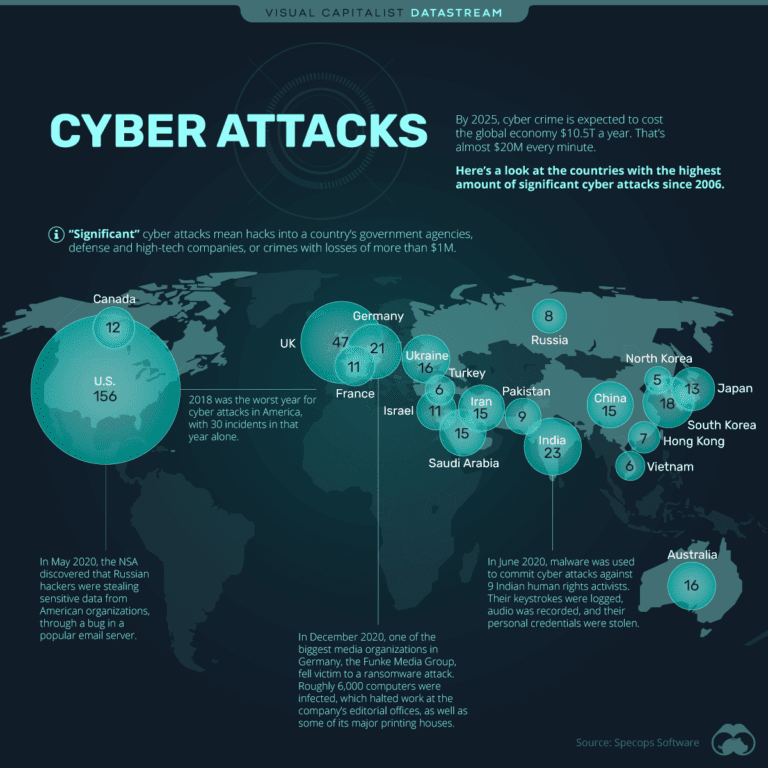
Everything seems to be easy and accessible in the Internet era but they are coming with a load of wireless network threats. Nowadays, we cannot deny that there are variations of threats around us, and we have no idea how the threats from wireless networks are really coming from.
In the generation of fast growing technology and innovation, it open the new opportunity for the skillful hackers ( cyber-crime ) to come up with the new techniques to access our privacy.
According to the statistics, the majority of the threats are coming from wireless network and smart devices because most people use these devices for cyber attack purposes such as unauthorized recording & monitoring, unauthorized accessing of confidential information and tracking personal areas.
But we have found the solution to end the threats from wireless network and empower solid countermeasure to reduce the loss.
Most of the threats are run by the variation of wireless signals such as Bluetooth, WiFi, and 3G/4G/5G because most people never realize that these kinds of signals can cost you by losing your personal privacy such as credit/debit card information, personal information and many more.
But do not worry, we already provide you a wide selection to prevent the threats from various kinds of wireless network.
Additional Topics
What is a wireless mobile network ?
Wireless mobile networking is designed to acquire all of the various technological innovations such as remote communication, transmission.
Nowadays, wireless mobile networks have the capability to do more activities such as transactions, entertainment, studying and making money by using only one smartphone.
The emerging wireless mobile networking are providing plenty of opportunities but there are also loads of hidden threats.
We are going to discuss it below.
Threats from the wireless mobile network
1. Traffic Eavesdropping
Known as a monitoring attack or theft of information as it is transmitted over a network by a computer, smartphone, or another connected device.
2. Lawful Interception
Lawful interception is a security process in which a service provider or network operator collects and provides law enforcement officials with intercepted communications of private individuals or organizations.
Or it means, they are tracking the conversation via phone calls for the security and legal investigating purposes.
But there are misused purposes by technical hackers, once your call is intercepted your conversation will not be private anymore.
Once you leave wireless mobile networks ( 4G, 4G LTE and 5G ) activated. It will open the opportunities for the hackers to eavesdrop on conversations, read texts, and track your smartphone location.
Bluetooth
Bluetooth is a short-range wireless technology standard that is used for exchanging data between fixed and mobile devices over short distances using UHF radio waves in the ISM bands.
Nowadays, everyday things are operated by Bluetooth such as headphones, speakers, smart devices and many more.
Dangerous threats from wireless Bluetooth network
Hackers use specific software which automatically detects nearby devices equipped with Bluetooth.
The hackers can access and attack your device with malware, spy on you and even steal your data from your text messages and apps.
1. Bluesnarfing
Bluesnarfing occurs when a hacker pairs with your Bluetooth device without your notice and steals or compromises your personal data.
Eavesdroppers trick you into pairing with their devices by misspelling the name of a device your device trusts.
For example, name their device the same name you have named your office printer and other stuff, so when you are searching the printer or stuff by using Bluetooth, you will access hackers’ Bluetooth you find and connect with first.
Once pairing, they can access your entire device. Always ensure that your Bluetooth device uses the latest software and protocols.
2. BlueBorne
BlueBorne is an attack virus that spreads through air and gets into a device via Bluetooth and can then take full control of the device.
BlueBorne can fulfill any malicious objective such as cyber espionage, data theft or even a ransomware attack.
It can also allow hackers to penetrate and access secure internal networks which are ‘air gapped’ meaning they are disconnected from any other network for protection thus endangering industrial systems, government agencies and critical infrastructure.
Then, air gapped computers are being targeted by the cyber criminals to penetrate the secure internal network and steal all the information stored in the air gapped computers.
3. Car Whispering
Traditional surveillance, by using the software that allows hackers to send and receive audio to and from a Bluetooth enabled car stereo system.
WiFi
A WiFi network is simply an internet connection that’s shared with multiple devices in a home or business via a wireless router.
Wi-Fi is the radio signal sent from a wireless router to a nearby device, which translates the signal into data you can see and use.
The device transmits a radio signal back to the router, which connects to the internet by wire or cable.
How does WiFi work ?
Wi-Fi uses radio waves to transmit data from your wireless router to your Wi-Fi enabled devices like your TV, smartphone, tablet and computer. Because they communicate with each other over the airwaves.
Dangerous Threats from WiFi & Wireless Network
Hackers have invented the new tactic “Air-Fi” method to hack an “Air-Gapped” computer.
This technique is enable attackers to steal information from air-gapped systems without requiring special hardware, physical access or network connectivity.
This technique is working by generating the WiFi signals around the air-gapped computers by infecting the malware to the target computer.
Once the “Air-Gapped” computer is infected. Attackers can use the AIR-FI technique to control the electrical current inside the RAM card on an air-gapped computer and turning it into a transmitter in Wi-Fi band 2.4 GHz in order to transmit the data to the receivers.
Air-gapped systems are ones commonly used on government, military and even high level corporate networks to store data that is considered to be incredibly sensitive, like classified files or (in the case of businesses) valuable intellectual property.
How your devices can be hacked even when you are offline.

1. Electromagnetic spying ( Radio signal hacked )
Electromagnetic spying technique is form of an eavesdropping in which special equipment is used to pick up side-band electromagnetic emissions from electronic devices that match to hidden signals or data to recreate these signals or data to spy on the electronic device.
Or it means the hackers will transfer your confidential information by using the radio waves.
If a spy wants to get the data, they could place a small device onto the target computer that infects the closed-off network with a piece of malware.
This malware can collect data on the infected network and send it via radio signals that every computer video card automatically generates.
Back in 2008, NSA used special devices, radio waves to spy on offline computers.
Here you can read for physical or solid countermeasures here
Normally, Faraday cage is created to protect this kind of hacking technique , but it still has a weakness due to various frequencies by the hackers. So, hackers are able to penetrate the Faraday cage by using devices with higher frequencies to attack the security of Faraday cage.
Luckily, our Tactical Countermeasure Signal Blockers – Military Grade have come up with the vary frequencies customized, you are able to create your own frequencies.
2. Air Hopper
Air Hopper technique is complex and only the most skilled hackers have any hope of actually executing it.
These attacks can target isolated machines and devices that have no connection to the Internet or your network.
By using radio signals and wireless communication to hack into an unconnected device and steal confidential corporate data.
Normally, this technique is designed to hack the confidential information from the “Air – gapped computer” by using radio frequencies instead of Bluetooth and WiFi.
Air gapped computers are computer systems or networks are not connected in any way to any other devices or networks in order to prevent from the wireless communication threats.
Air gapped computers are used to store the large amount confidential information.
Air Hopper Demonstration
According to the demonstration, Air hopper technique did not rely on the network, SIM card and WiFi for transmitting the data
Notes : Modern hackers have been working hard on research to make this method become much easier than usual in the upcoming future.
Experimented by Cyber Security Labs at Ben Gurion University
3. AIR - FI Technique
AIR-FI is a hacking technique that use to steal data even from air-gapped computers.
Hacker will generate electromagnetic waves as some type of electric current passes through it. Because Wi-Fi signals are radio waves, and radio waves and electromagnetic waves are very similar.
AIR – FI Technique is emitting the electromagnetic emissions in the 2.4 GHz Wi-Fi band to deploy specially designed malware on the target machine.
Once the machine exploited by malware, the “AIR-FI” will control the electrical current inside the RAM card on an air-gapped computer and turning it into a transmitter in Wi-Fi band 2.4 GHz.
So the hacker needs to infect a device with a WiFi interface in the area of the air-gapped target by generating the covert WiFi signals from “Air – gapped computers”.
AIR-FI Technique Demonstration
Conclusion : This technique is generating the WiFi signals around the air-gapped computers by infecting the malware to the target computer
The attack does not require hardware components to interact with Wi-Fi installed on the computers under attack.
Once the air gapped is infected, the confidential information is in danger
Notes : This technique is still currently in the development process, but it will create devastating threats to society in the future.
Good news : This can be prevented by using the jamming method, and we have come up with the tactical jamming solutions to tackle this kind of threat before it accesses your confidential information.
Experimented by Cyber Security Labs at Ben Gurion University.
4. USBee
This technique is turned the targeted computer’s USB ports into mini Radio Frequency (RF) transmitters by adjusting the data fed at high-speed to plugged-in devices.
This kind of technique is also modified USB device and allowed spies to transmit data out of targeted computers through electromagnetic signals.
In 2016, researchers have developed software that goes another level by turning unmodified USB devices into covert transmitters that can transmit large amounts of information out of similarly “air-gapped” PCs.
Experimented by Cyber Security Labs at Ben Gurion University.
I DO NOT OWN THE RIGHTS TO THE CLIPS OR MUSIC. ALL RIGHTS BELONG TO THEIR RESPECTFUL OWNERS.
This video is not intended to violate any Condition of Use.
Copyright Disclaimer Under Section 107 of Copyright Act 1976, allowance is made for “fair use” for purposes such as criticism, comment, news reporting, teaching, scholarship, and research.
Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favour of fair use.