In Switzerland, where financial security is a top priority, safeguarding your business from espionage threats is essential. Join Archthetic as we dive into the critical role of TSCM in finance, explore how it strengthens security standards, ensure compliance with legal regulations, and address the unique cultural factors influencing security practices. Our commitment is to redefine industry norms and provide unparalleled protection to Switzerland’s financial sector.
Why Archthetic Expanded into the Swiss TSCM Market : A Response to Espionage Threats

The Swiss Federal Intelligence Service (FIS) authorized the credible Institute for Criminal Law and Criminology at the University of Bern to investigate the scale of industrial espionage in Switzerland. Astonishingly, about one-third of surveyed companies disclosed falling prey to industrial espionage, likely victims of unauthorized technical surveillance, known as “bugging,” during these covert operations.
The financial impact of these activities is substantial, with a significant 11% of these companies facing a real risk of going out of business.
This isn’t just a problem in Switzerland; other European nations have found similar results.
The widespread nature of these espionage threats highlights the urgent need for better security measures. Archthetic’s decision to expand into the Swiss TSCM market is a response to these challenges, aiming to offer effective solutions and protect businesses from potential risks.
TSCM Matters in the Switzerland Financial & Economic Context
1. Protecting Financial Institutions:
- As a financial powerhouse, Switzerland is a prime target for espionage. TSCM safeguards banks and financial institutions, preserving the integrity of transactions and confidential client information.
2. Preserving Trade Secrets:
- In a nation deeply involved in global trade, TSCM helps protect Swiss companies’ trade secrets, securing economic interests and maintaining a competitive edge on the international stage.
3. Ensuring Data Privacy Compliance:
- Switzerland, known for its commitment to data privacy, requires businesses to adhere to stringent regulations. TSCM assists in ensuring compliance, mitigating the risk of unauthorized surveillance and potential legal ramifications.
TSCM in the Financial Sector

Safeguarding Client Confidentiality:
- TSCM is indispensable for financial institutions to safeguard client confidentiality. Electronic sweeps and bug detection technologies ensure that sensitive discussions remain private, preserving trust in the financial sector.
Mitigating Corporate Espionage Risks:
- With corporate espionage posing a substantial threat to financial stability, TSCM becomes a strategic tool to identify and neutralize potential risks, protecting vital financial information from falling into the wrong hands.
Complementing Cybersecurity Measures:
- TSCM and cybersecurity go hand in hand. By integrating these measures, financial entities in Switzerland can establish a holistic defense against both physical and digital threats, ensuring comprehensive protection.
Understanding TSCM in Switzerland
In Switzerland, TSCM isn’t a luxury – it’s a necessity for every business. Archthetic’s mission is to highlight the vital role of TSCM in protecting your operations from covert surveillance.
Our TSCM kit is your shield against illegal surveillance, and we’re here to support newcomers entering the TSCM landscape.
Empowering TSCM Growth in Switzerland : What Archthetic Offers
Wireless Signal Scanning for Financial Security and Transaction Protection
Wi-Fi Eavesdropping:
- Risk: Attackers intercept unencrypted financial transactions and credentials exchanged over unsecured or public Wi-Fi networks.
- Solution: WAM-X10 Wireless Activity Monitor detects unauthorized access to Wi-Fi networks, ensuring that sensitive information is encrypted and not vulnerable to eavesdropping.
Rogue Hotspots:
- Risk: Malicious actors set up fake Wi-Fi networks (rogue hotspots) to trick users into connecting, allowing them to intercept sensitive information.
- Solution: WAM-X10 Wireless Activity Monitor identifies rogue access points, ensuring devices connect only to legitimate, secure networks.
Bluetooth Hacking:
- Risk: Exploiting unsecured Bluetooth connections to intercept financial transactions made through mobile devices.
- Solution: WAM-X10 Wireless Activity Monitor monitors Bluetooth signals to detect unauthorized devices attempting to pair with mobile phones, ensuring secure financial transactions.
Man-in-the-Middle (MitM) Attacks:
- Risk: Attackers intercept communications between two parties to manipulate or steal financial data during wireless transactions.
- Solution: WAM-X10 Wireless Activity Monitor identifies anomalies in communication patterns, such as sudden interruptions or rerouted signals, indicating potential MitM attacks.
Wireless Data Leakage:
- Risk: Sensitive financial data being accidentally broadcasted or leaked over wireless networks, exposing private information.
- Solution: WAM-X10 Wireless Activity Monitor ensures that no unauthorized data is transmitted, scanning for accidental leaks and providing alerts to prevent unauthorized access.
Mobile Payment Interception:
- Risk: Cybercriminals intercept mobile payment signals from smartphones or contactless cards, potentially compromising payment data.
- Solution: iProtect Defender EZ 10 GHz RF Detector detects unauthorized attempts to intercept signals from mobile devices and payment terminals, safeguarding transactions.
GPS Spoofing:
- Risk: Fraudsters use GPS spoofing to mislead financial services into accepting fraudulent transactions.
- Solution: CAM-GX5 Cellular Activity Monitor detects discrepancies in GPS signals, ensuring that only legitimate location data is used in verifying transactions.
NFC (Near-Field Communication) Attacks:
- Risk: Hackers exploit NFC vulnerabilities to steal data from wireless credit cards or mobile devices during contactless payments.
- Solution: WAM-X10 Wireless Activity Monitor detects rogue NFC signals attempting to interfere with legitimate communications, preventing unauthorized access.
Wi-Fi Pineapple Attacks:
- Risk: Attackers use a “Wi-Fi pineapple” device to mimic a legitimate Wi-Fi network and intercept financial data.
- Solution: WAM-X10 Wireless Activity Monitor detects and blocks these sophisticated attack devices, preventing interception of sensitive communications.
Cellular Signal Hijacking:
- Risk: Hackers exploit cellular networks to intercept calls or text messages containing two-factor authentication codes or other sensitive information.
- Solution: CAM-GX5 Cellular Activity Monitor identifies unusual cellular signals, preventing unauthorized interception of authentication codes.
Cryptocurrency Transaction Interception:
- Risk: Attackers exploit weak wireless encryption to intercept and steal cryptocurrency transaction data, leading to the loss of digital assets.
- Solution: WAM-X10 Wireless Activity Monitor identifies vulnerabilities in wireless connections used for cryptocurrency transactions, ensuring digital assets remain secure.
Signal Jamming and Denial of Service (DoS):
- Risk: Cybercriminals use signal jamming techniques to block or disrupt wireless communication, hindering financial transactions or ATM services.
- Solution: WAM-X10 Wireless Activity Monitor detects unusual activity and jamming attempts, allowing financial institutions to respond swiftly and restore communication channels.
Understanding Unauthorized RF Signals in Financial and Cryptocurrency Transactions
Unauthorized RF Signals and Their Implications:
13.56 MHz Signals:
- Context: Widely used in contactless payment systems and certain cryptocurrency hardware wallets.
- Unauthorized Use: Attackers can deploy skimming devices operating at this frequency to wirelessly capture card or wallet information without the user’s knowledge.
- Detection: Unexpected 13.56 MHz signals near transaction points or wallet interactions may indicate unauthorized interception attempts.
- Detection Tools:
- Professional Digital RF Detector: Capable of detecting signals across a broad frequency range, including 13.56 MHz. Features include silent alert modes and dual antenna options for comprehensive detection.
2.4 GHz Signals:
- Context: Commonly utilized in various wireless communication protocols, including some used in stock trading platforms and cryptocurrency transactions.
- Unauthorized Use: Attackers can exploit this frequency band to interfere with or intercept communications between trading systems or cryptocurrency exchanges.
- Detection: Anomalies in 2.4 GHz RF activity near financial transaction points may suggest malicious interference or data interception efforts.
- Detection Tools:
- RF Wireless Signal Detector Wand: Designed to swiftly identify hidden devices operating within the 2.4 GHz range. Features include a discreet design suitable for covert sweeps and efficient detection capabilities.
High-Frequency (HF) Signals (900 MHz and Above):
- Context: Certain financial applications and devices operate on frequencies above 900 MHz.
- Unauthorized Use: Malicious actors can exploit these frequencies to eavesdrop on communications or disrupt services related to stock market data transmission or cryptocurrency trading.
- Detection: Unauthorized signals in these frequency ranges can indicate potential security threats to financial communications.
- Detection Tools:
- Professional Digital RF Detector: Effective in detecting a wide range of frequencies, including those above 900 MHz. Offers features such as silent alerts and dual antenna options for precise detection.
Mitigation Strategies:
- Encryption: Employ robust encryption methods to protect data transmitted over RF channels, ensuring that intercepted data remains unreadable.
- Real-Time Monitoring: Utilize advanced monitoring tools to detect anomalies in RF activity, enabling early identification of unauthorized signals.
- Authentication Protocols: Implement strong authentication mechanisms to verify the legitimacy of devices and users accessing financial systems.
- Physical Security Measures: Use shielding techniques, such as Faraday cages, to block unauthorized RF signals from accessing sensitive areas.
Conclusion:
Understanding and monitoring unauthorized RF signals are crucial for protecting the integrity of financial transactions, including those in cryptocurrencies and stock markets. By implementing comprehensive security measures and utilizing specialized detection tools, individuals and organizations can mitigate the risks associated with RF signal-based threats and ensure the confidentiality and reliability of their financial communications.
Electronic Bug Detection in Financial Security
Securing Financial Sector: How Bug Detectors Protect Information
1. Trade Secrets and Business Strategies:
- Solution: Bug detectors prevent unauthorized capture of trade secrets and business strategies by identifying hidden recording devices.
2. Client and Customer Information:
- Solution: Detecting bugs safeguards discussions containing client details, ensuring confidentiality and protection from eavesdropping.
3. Market Strategies and Investments:
- Solution: Regular bug sweeps secure discussions on market strategies and investments, maintaining the confidentiality of crucial information.
4. Mergers and Acquisitions (M&A) Plans:
- Solution: Bug detectors protect sensitive information about potential mergers and acquisitions, preventing unauthorized access.
5. Sensitive Meetings and Board Discussions:
- Solution: Bug detectors in meeting rooms prevent eavesdropping on high-level board meetings and executive discussions.
6. Financial Compliance Strategies:
- Solution: Bug detectors secure discussions on compliance strategies, ensuring confidential information remains protected.
7. Technology and Security Measures:
- Solution: Detecting bugs protects information on technological infrastructure and security measures, preventing unauthorized access.
8. Internal Policies and Procedures:
- Solution: Bug detectors secure discussions about internal policies and procedures, preserving information crucial for governance.
9. Financial Forecasts and Projections:
- Solution: Bug detectors protect discussions on financial forecasts and projections, ensuring confidentiality.
10. Employee Personal Data: – Solution: Identifying bugs safeguards discussions containing sensitive HR-related information, protecting employee privacy.
11. Customer and Investor Confidence: – Solution: Bug detectors secure discussions on financial stability and risk management, preserving customer and investor confidence.
In summary, bug detectors play a pivotal role in proactively protecting sensitive information in the financial sector, ensuring confidentiality and trust. Regular sweeps contribute to a robust security posture, mitigating risks and preserving the integrity of financial operations.
Transaction Eavesdropping Protection of Financial & Cryptocurrency Data
Securing Financial Conversations: Defeating Eavesdropping with White Noise and Ultrasonic Waves
Client Privacy:
- Solution: White noise and ultrasonic waves protect client meetings, ensuring privacy and confidentiality.
Trade Secrets and Strategies:
- Solution: White noise shields internal meetings discussing proprietary financial strategies, safeguarding trade secrets.
M&A Confidentiality:
- Solution: Eavesdropping defeater with white noise secures M&A discussions, enhancing confidentiality.
Secure Account Information:
- Solution: White noise conceals account details, preventing unauthorized capture of sensitive financial information.
Insider Information Prevention:
- Solution: Eavesdropping defeater disrupts attempts to capture insider information during discussions.
PII and Identity Protection:
- Solution: White noise safeguards personal and financial details, preventing identity theft risks.
Credit and Risk Data Security:
- Solution: White noise protects discussions related to credit assessments and risk evaluations.
Regulatory Compliance Assurance:
- Solution: White noise shields compliance and regulatory discussions, ensuring confidentiality.
FinTech IP Protection:
- Solution: Eavesdropping defeater with white noise safeguards discussions on proprietary FinTech solutions.
KPI Confidentiality:
- Solution: White noise conceals financial KPI discussions, ensuring the privacy of strategic planning.
Deploying eavesdropping defeater technology with white noise and ultrasonic waves creates a secure auditory environment, effectively protecting financial conversations from unauthorized interception.
Uncover Hidden illegal Surveillance Cameras in Financial Environments
Safeguarding Swiss Finance: How Camera Lens Finder Neutralizes Threats
Espionage Defense:
- Detects hidden cameras, preventing internal and external actors from conducting espionage within financial institutions.
Restricted Area Security:
- Identifies unauthorized hidden cameras, ensuring the protection of restricted financial areas and maintaining overall institution security.
Confidential Financial Discussions:
- Neutralizes the risk of capturing sensitive financial discussions, preserving client confidentiality and safeguarding strategic information.
Client Privacy Assurance:
- Detects hidden cameras in meeting rooms and client service areas, reinforcing trust by assuring clients of the confidentiality of their financial matters.
Protection Against Intellectual Property Theft:
- Guards against the theft of trade secrets and intellectual property by identifying hidden cameras attempting to capture proprietary information.
Compliance and Regulatory Standards:
- Supports adherence to strict compliance and regulatory standards by preventing activities captured by hidden cameras that might violate regulations.
Fraud Prevention:
- Mitigates social engineering and fraud risks by identifying hidden cameras used for deceptive means, safeguarding against unauthorized access and fraudulent activities.
Reputation Management:
- Preserves the reputation of financial institutions by proactively addressing hidden camera threats, instilling confidence among clients and stakeholders in the security of their financial dealings.
In summary, the Camera Lens Finder acts as a strategic defense tool, swiftly identifying and neutralizing hidden camera threats in the Swiss financial sector. Its proactive approach reinforces security, protects client confidentiality, and upholds the integrity of financial operations.
6. Global Quality Standards :

FCC Compliance
Pioneering Connectivity in Security

CE Marking
Elevating Security Standards in Europe

UKCA Certification
Trusted Surveillance in the United Kingdom
Our TSCM equipment complies with international quality benchmarks, meeting the needs of businesses not only in Switzerland but also globally.
Our imported products are duly certified by FCC, CE, and UKCA.
TSCM Tasks and How Archthetic's Tools Simplify the Process
In executing critical TSCM tasks, Archthetic’s advanced tools are designed to make the process easier and more efficient :
1. Threat Analysis :
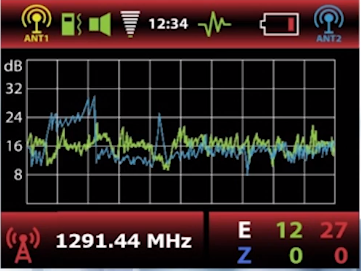
– Archthetic’s surveillance detection devices provide real-time threat analysis, allowing TSCM professionals to swiftly identify and assess potential risks.
2. Vulnerability Assessments :
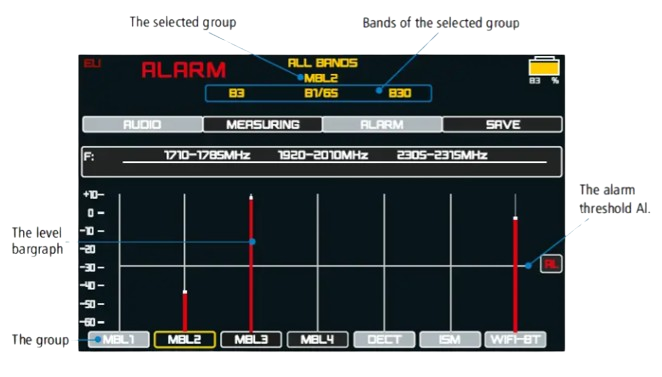
– Our bug detection solutions offer comprehensive vulnerability assessments, ensuring a thorough examination of potential weaknesses in your security infrastructure.
3. Provide Corporate Espionage Threat Briefs :
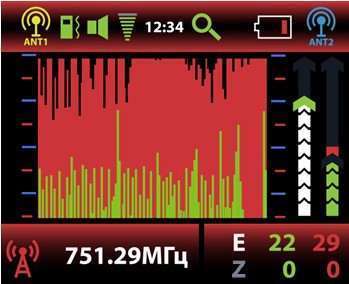
– Archthetic’s strategic partnerships and continuous monitoring enable us to provide timely and insightful corporate espionage threat briefs, keeping businesses informed and prepared.
4. TSCM to Secure Confidential/Sensitive Meetings :
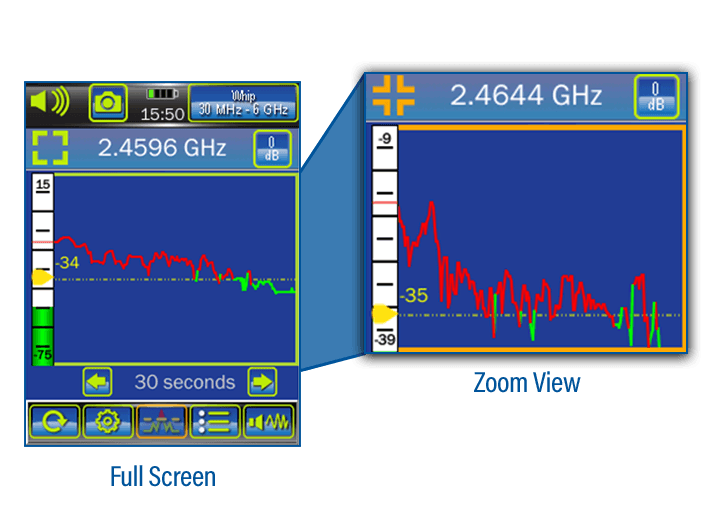
– With Archthetic’s tailored TSCM solutions, businesses can confidently secure confidential and sensitive meetings, mitigating the risk of eavesdropping or surveillance.
5. Conduct Essential Routine TSCM Surveys :

– Our electronic sweeps and surveillance detection devices empower TSCM professionals to conduct routine surveys efficiently, ensuring ongoing security vigilance.
Archthetic’s commitment to excellence extends to providing tools that simplify and enhance the execution of these essential TSCM tasks, offering businesses a robust defense against potential threats.
TSCM Laws & Compliance in Switzerland : A Legal Framework for Security
Switzerland, known for its commitment to privacy and security, has stringent laws governing TSCM practices. Archthetic ensures compliance with these regulations, providing businesses with confidence in their security measures. Key aspects of TSCM laws and compliance in Switzerland include :
1. Legitimate Processing and Transparency :
TSCM activities, including electronic sweeps and bug detection, must have a legal basis, ensuring that the processing of data during surveillance is legitimate. Transparency in communicating the purpose and methods of TSCM operations aligns with the principles of fairness and lawfulness.
2. Purpose Limitation and Data Minimization :
TSCM practitioners adhere to the principles of purpose limitation, collecting and processing personal data only for the explicit purpose of identifying and neutralizing surveillance threats. Data minimization ensures that only necessary information is processed, limiting the scope of TSCM activities to what is essential.
3. Individual Rights in TSCM :
Individuals subject to TSCM activities have the right to be informed about the processing of their data, mirroring the right to information. Additionally, TSCM providers must respect individuals’ rights to correction or deletion of inaccurate or outdated information, enhancing the protection of privacy.
4. Data Security in TSCM :
TSCM equipment and practices must align with Swiss data protection regulations by implementing robust security measures. This ensures that personal data collected during surveillance is safeguarded against unauthorized access, maintaining the confidentiality of sensitive information.
5. Cross-Border Data Transfers in TSCM :
TSCM providers conducting operations that involve cross-border data transfers must adhere to Swiss regulations governing such transfers. Employing mechanisms like standard contractual clauses ensures that data is adequately protected when shared internationally.
6. TSCM Compliance and Data Protection Officers :
Organizations engaging in extensive TSCM activities may find it beneficial to appoint a Data Protection Officer (DPO) to oversee compliance with both TSCM-specific regulations and broader data protection laws. This ensures a comprehensive approach to safeguarding personal data.
7. Ethical and Responsible TSCM Practices :
TSCM, as part of the broader legal framework, must operate ethically and responsibly. Practitioners are expected to conduct their activities in alignment with data protection laws, respecting the rights and privacy of individuals subject to surveillance countermeasures.
Challenging the Status Quo in Switzerland's Financial Sector
Switzerland is globally recognized as a leader in the financial sector. Archthetic aims to challenge the status quo and strengthen the financial sector’s reputation for security in Switzerland. By introducing advanced TSCM solutions tailored for the financial industry, we contribute to enhancing the overall security posture of Switzerland’s financial sector, safeguarding sensitive information and maintaining the country’s standing as a trusted financial hub.
Closing the Loop : Archthetic - Your Path to TSCM Success in Switzerland
As the demand for Technical Surveillance Countermeasures (TSCM) grows in Switzerland, www.archthetic.com becomes pivotal, not just in providing TSCM kits but also fostering growth opportunities for businesses entering the TSCM market. Our commitment goes beyond products; it extends to empowering you with knowledge and support.
Choose Archthetic, and together, let’s secure your business and unlock the potential for TSCM growth in Switzerland.





Archthetic’s plans and research on safeguarding Switzerland’s financial sector are truly impressive.
We’ve also planing to establish an in-house TSCM team to ensure top-notch security for our clients.
We’re eager to explore opportunities for sponsored content or link placements on Archthetic’s website to showcase our security measures and commitment to protecting client assets.
Could you please share more details on how we can collaborate for such promotional initiatives ?