
In this blog post, we’ll delve into why logistics businesses need Technical Surveillance Countermeasures (TSCM) services and the specific threats they should be aware of.
In the fast-paced world of logistics, where the smooth flow of goods and information is paramount, ensuring the security of operations is of utmost importance.
Logistics businesses, in particular, face various threats related to surveillance, making it crucial to be proactive in implementing measures to safeguard against potential risks.
Topics
The Need for TSCM in Logistics :
1. Intellectual Property Protection :
Logistics businesses often handle proprietary processes and technologies. TSCM services help thwart attempts at corporate espionage by detecting and neutralizing electronic eavesdropping devices that could compromise intellectual property.
2. Supply Chain Integrity :
Surveillance threats can lead to disruptions in the supply chain through theft, sabotage, or other malicious activities. TSCM services play a vital role in identifying and mitigating these risks, ensuring the continuity and reliability of logistics operations.
3. Data Breach Prevention :
Sensitive customer information, shipment details, and financial data are prime targets for surveillance. TSCM services help prevent data breaches by securing wireless signals and identifying hidden cameras that could compromise confidential information.
4. Counterfeit Goods and Smuggling :
Hidden cameras and surveillance devices may be deployed to monitor logistics activities for illegal purposes. TSCM services assist in detecting and neutralizing these devices, preventing activities such as smuggling or the transportation of counterfeit goods.
5. Insider Threat Mitigation :
Employees with access to sensitive information can pose a threat if coerced or tempted to share information. TSCM services provide a layer of protection against insider threats by identifying unauthorized surveillance devices and potential vulnerabilities.
6. Competitive Intelligence Gathering :
Competitors may employ surveillance tactics to gain insights into pricing strategies, contract negotiations, or upcoming business ventures. TSCM services help logistics businesses maintain a competitive edge by safeguarding against unauthorized information gathering.
7. Regulatory Compliance :
Logistics businesses must comply with privacy laws and industry regulations. TSCM services contribute to regulatory compliance by ensuring that surveillance activities within the organization adhere to legal standards.
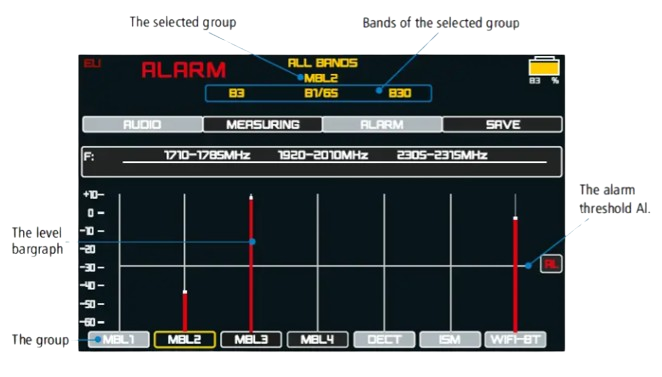
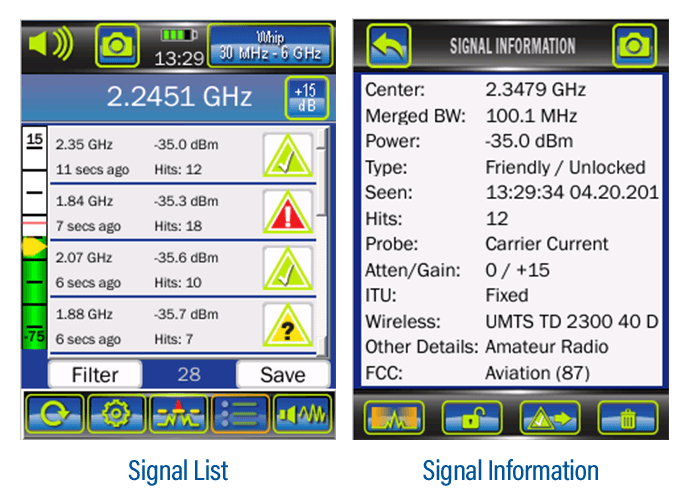
Wireless Signals and Hidden Cameras : Key Threats to Address
1. Data Security :
2. Tracking and Monitoring :

Hidden cameras and wireless devices can be used for unauthorized tracking and monitoring of logistics operations, jeopardizing the security and confidentiality of shipments, routes, and warehouse activities.
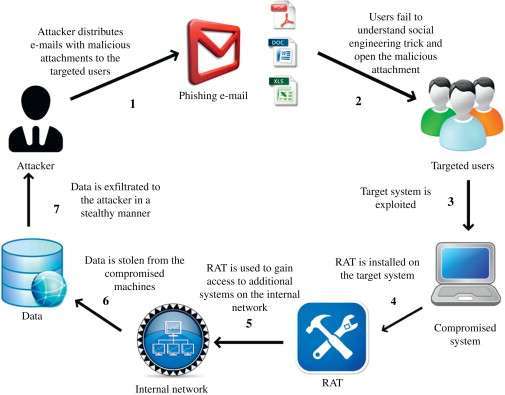
3. Corporate Espionage :
Competitors or external actors may exploit wireless signals and hidden cameras to gather intelligence on logistics processes, pricing strategies, or supply chain details. TSCM services are instrumental in preventing corporate espionage.
4. Insider Threats:
Employees with malicious intent might leverage hidden cameras or exploit wireless vulnerabilities. Awareness allows businesses to implement countermeasures, mitigating the risk of insider threats.
Note : The red dot you see is hidden camera detected by WEGA hidden camera detector
5. Privacy Concerns :
Adhering to privacy regulations and ethical considerations is essential. Logistics businesses need to be mindful of potential privacy issues related to hidden cameras or surveillance through wireless signals.
Note : The red dot you see is hidden camera detected by SPYFINDER PRO
6. Smuggling and Theft Prevention :
Hidden cameras may facilitate smuggling or theft within logistics operations. Detecting and neutralizing these devices is vital for preventing illicit activities that could compromise the integrity of the supply chain.
Note : Red dot you see is the hidden camera detected by WEGA hidden camera detector – TSCM Grade
Case Study : Recommendations for FedEx Corporation

Challenge :
Detection and Mitigation of Wireless Signals and Hidden Cameras
Background :
FedEx, as a global logistics giant, handles millions of shipments daily, making it a prime target for potential surveillance threats. The company faced challenges related to protecting sensitive shipment data, preventing intellectual property theft, and ensuring the security of its vast network.
Approach :
FedEx implemented a comprehensive strategy to address wireless signals and hidden camera threats :
3. Technology Integration :
Action : Invest in advanced security technologies, including encrypted communication systems, secure networks, and anti-surveillance technology.
Outcome : Strengthen the overall security infrastructure, making it more resistant to potential surveillance threats.
4. Continuous Monitoring and Updates :
Action : Establish a continuous monitoring system for detecting anomalies in wireless signals and potential hidden cameras. Regularly update security protocols.
Outcome : Enable real-time response to emerging threats, maintaining an adaptive and resilient security posture.
5. Collaboration with External Experts :
Action : Engage external TSCM experts for periodic assessments and to provide insights into evolving surveillance threats.
Outcome : Benefit from specialized knowledge and experience, enhancing the effectiveness of security measures.
6. Establish a Security Culture :
Action : Promote a security-conscious culture within the organization, emphasizing the importance of individual responsibility in maintaining security.
Outcome : Foster a collective commitment to security, with employees actively contributing to the overall safety of FedEx operations.
Cost-Effective TSCM Strategy : FedEx

1. Prioritize High-Risk Areas :
Strategy : Focus TSCM efforts on high-risk areas, such as facilities handling sensitive shipments or key communication nodes.
Outcome: Maximize the impact of TSCM measures by allocating resources where they are most needed.
2. Implement Risk-Based Frequency :
Strategy : Conduct TSCM assessments based on risk assessments. High-risk areas may require more frequent evaluations than lower-risk locations.
Outcome : Optimize budget utilization by allocating resources based on the level of risk, ensuring a proportional response.
3. Training and Empowering Internal Teams :
Strategy : Invest in training internal teams to perform routine TSCM tasks.
Outcome : Build in-house expertise, reducing the reliance on external experts for routine assessments and potentially lowering long-term costs.
4. Leverage Open-Source Solutions :
Strategy : Explore cost-effective, open-source TSCM tools and technologies.
Outcome : Reduce technology acquisition costs while still maintaining a strong security posture.
5. Engage in Information Sharing Networks :
Strategy : Participate in industry information-sharing networks to stay updated on emerging threats.
Outcome : Access valuable threat intelligence without incurring significant costs, enhancing the effectiveness of TSCM efforts.
6. Continuous Improvement :
Strategy : Establish a feedback loop for continuous improvement in TSCM practices.
Outcome: Learn from each assessment, refine strategies, and ensure that TSCM efforts remain cost-effective and aligned with evolving threats.
By implementing these practical solutions and a cost-effective TSCM strategy, FedEx can significantly enhance its security posture against wireless signals and hidden camera threats without imposing a substantial burden on the overall budget.
Cost-Effective TSCM tools
- All
- Gallery Item
By implementing these practical solutions and a cost-effective TSCM strategy, FedEx can significantly enhance its security posture against wireless signals and hidden camera threats without imposing a substantial burden on the overall budget.
Cost-Effective TSCM Tools for Improving Logistics Business :
3. User-Friendly Interface :

Feature : Intuitive and easy-to-use interfaces for logistics personnel.
Benefit : Reduces training time, ensuring quick adoption and seamless integration into daily operations.
4. Multi-Platform Compatibility :
Feature : Compatibility with various devices and operating systems.
Benefit : Provides flexibility, allowing logistics teams to use the tools on different platforms, enhancing accessibility and convenience.
5. Customizable Threat Analysis:
Feature : Customizable threat analysis based on specific logistics needs.
Benefit : Tailors security measures to address industry-specific challenges, optimizing the effectiveness of the TSCM tools.
6. Scalability and Upgradability :
Feature : Scalable solutions that can grow with the expanding logistics business.
Benefit : Ensures long-term viability and adaptability, accommodating the evolving needs of the logistics industry.
7. Integration with Existing Security Infrastructure :
Feature : Seamless integration with existing security systems.
Benefit : Streamlines operations by leveraging existing infrastructure, minimizing disruptions and reducing implementation costs.
8. Encryption and Secure Communication :
Feature : Robust encryption protocols for secure communication.
Benefit : Safeguards sensitive logistics data, protecting against unauthorized access and potential breaches.
9. Comprehensive Reporting and Analytics :
Feature : Detailed reporting and analytics tools.
Benefit : Provides valuable insights into potential threats and vulnerabilities, empowering logistics managers to make informed decisions and enhance overall security.
10. Cost-Efficiency and Return on Investment (ROI) :
Feature : Affordable pricing models with a clear ROI.
Benefit : Maximizes the value of the TSCM tools, ensuring that the investment contributes positively to the bottom line of the logistics business.
Implementing cost-effective TSCM tools with these outstanding features can significantly improve the security posture of a logistics business, mitigating risks and safeguarding critical assets and information.
In conclusion, the deployment of cost-effective Technical Surveillance Countermeasure (TSCM) tools presents a pivotal opportunity for the logistics industry to bolster its overall security and operational efficiency. By incorporating advanced features such as real-time monitoring, customizable threat analysis, and seamless integration, logistics businesses can fortify their defenses against potential threats.















New updated on 7th June 2024