Targeted by surveillance devices ?
Nowadays, privacy is the most powerful asset because everything is easily accessible and privacy is not in safe hands anymore. You may feel that you are being targeted, tracked and monitored by someone or surveillance devices.
There are several techniques that people use to access your privacy.
According to the statistics, due to the rapid growth of innovation, the use of surveillance devices have significantly risen and are expected to grow more year after year.
As I mentioned above, everything is easily accessible. The surveillance (spy) products have been widely sold in the worldwide market right now.
So you will never realize that you are being tracked, monitored and targeted by surveillance devices because the new surveillance items have been designed to track,monitor and target you from the blind spot.
We have implemented the tactical detection to protect your privacy from being tracked, monitored and targeted by unknown parties & surveillance devices.
Why detection is matter :
1. Protect you from the unauthorized monitoring
2. Prevent the unfair competition between the companies
3. Eliminate the insecure environment
Topics
Covert Threats

Covert threats in our definition mean the covert surveillance products that you have seen or touch it but never realize about.
Nowadays, there are many built-in editions of tracking and monitoring and spying devices that are selling in the market.
Actually, those devices are built to optimize the strategy for the law enforcement and the related department to perform the crucial mission. Due to the growth of distribution channels and market demand, these items are widely selling on every platform today.
Everyone can access and buy it from everywhere. So it’s a hard task for us to identify the personal’s purposes.
Some people may use it to improve their security level and some people may use it to invade others’ privacy.
Covert Spying Devices
1.Covert Wireless / Spy / Wifi camera
Best selling items in the worldwide market today, these items are designed to formulate the extra spot to optimize security. But there are several misused in this item in unauthorized monitoring like invading others’ privacy, sexual harassment for blackmail purposes and seeking for confidential activities like secret negotiations and confidential meeting.
Notes : Theses items have been come up with the built-in edition of daily use items such as alarm clock, cable box, mouse, speaker, charger and many more.
2.Modern bugs
Another accessible item for everyone, these items have come up with a small design to place in the blind spot and able to listen from anywhere.
These items are also built as covert editions in the worldwide market but only few will know the actual distribution channel of this product.
These items have been misused by several users for the unauthorized monitoring, tracking of privacy and confidential conversation.
3.Audio / Voice transmitter
Working similar with the bugs but in limited range. Mostly used in the organization, law enforcement, military and household to monitor the abnormal internal activities.
4.GPS Transmitter
Nowadays, most GPS trackers have come up with the differentiation of size and new functions with voice monitoring which means they are able to track your location and monitor your conversation during the trip as well.
Invisible Cyber threats
Nowadays, we do not realize that we have been surrounded with a load of unseen threats such as threats from wireless signal and RF signal. All of them are considered as a huge role to perform the cyber attacks.
This is the dark side of innovation that we are facing because several hackers have developed the hacking techniques to steal your confidential information and monitor your activities from somewhere.
Worse than that, traditional security products ignore RF protocols in the air and wait for issues to show up as symptoms on the network.
Corporations, TSCM and governments can’t counteract what they can’t detect due to the lack of accurate information about the RF environment. Then they are easily being targeted by the cyber criminals.
Vulnerable wireless and cellular devices are currently playing as everyday devices inside government facilities , valuable place and in enterprises.
These rogue devices can include building controls, cell phones, medical devices, printers, security cameras, smart TVs and more.
1. Air Hoppers technique
Air Hoppers technique was founded in 2014 and is potentially in the developing process now. This kind of invisible threat will be the most dangerous attack in the upcoming future even though you leave your devices offline but the hackers will use the radio signal to transmit your data.
AirHopper is a special type of keylogger because it uses radio frequencies to transmit data from an air-gap computer.
This technique is developed to penetrate the security measure of the air-gap computer by transmitting confidential information from an offline ( Air-Gap ) computer.
2. Burst Transmission
A burst transmission technique is to transmit data over a long range in secure mode for making a difficult for enemy Direction Finding systems to locate the radio as it transmits for a short duration that is only when required.
Normally, this technique is used by authorized private investigator and military to collect the information from the enemies in order to monopolize the advantage.
But there are misused by the modern hackers to eavesdrop and steal your data by using this kind of technique to track and monitor your privacy.
The system is dependent on the radio interface for transmission of data by using VHF transmission.
You can also check out our Threats From Wireless Network & How your devices can be hacked by wireless network page for additional information about the threats from wireless signal and the products for eliminating the radio transmission threats.
3. BlueBorne
BlueBorne is an attack virus that spreads through air and gets into a device via Bluetooth and can then take full control of the device.
BlueBorne can fulfill any malicious objective such as cyber espionage, data theft or even a ransomware attack.
It can also allow hackers to penetrate and access secure internal networks which are ‘air gapped’ meaning they are disconnected from any other network for protection thus endangering industrial systems, government agencies and critical infrastructure.
Then, air gapped computers are being targeted by the cyber criminals to penetrate the secure internal network and steal all the information stored in the air gapped computers.
You can also check out our page for additional information about the threats from wireless network and the products for eliminating the radio transmission threats.
Our signal & threats blocker range can also empower your security measures by disrupting all those wireless signal threats from accessing your confidentiality and trade secret.
Signs of being targeted by surveillance devices
-
1. People seem to know your activities in advanced.
-
2. Confidential business or professional trade secrets being imitated by competitors or other parties.
-
3. Having the extra stuffs in your place.
-
4. Bugging devices may come in form of gifts ( covert bugging devices ).
- 5. Your belonging have moving from another place to another place.
Current Problems
Privacy invader rate has been significantly increased year after year even in pandemic situations.
Inappropriate activities have been leaked to the public such as sexual activity and internal family issues.
Rise of blackmail actions & privacy leaked
Confidential information and actions have been leaked frequently, occurring especially in business organizations, law enforcement,law firms, military and state government agencies. Which means they are facing with internal traitors and unidentified external threats.
Rise of disrupting human rights in every public place such as hotel, restaurant, cinema, etc.
The uses of surveillance devices have significantly risen in the market and are expected to grow more year after year.
And also come up with the several drawbacks such as :
Increase in privacy concern.
Increase in adoption towards spy and hidden cameras.
Illegal and unfair competition between the companies.
Potential problems
Increasing of unauthorized monitoring and tracking
Increasing of criminal rate
Insecure environment ( Feeling of being tracked, targeted and monitored )
Rise of new age threats
Detection line up - TSCM Grade
-
Out of stockOut of stockOut of stockOut of stockOut of stockOut of stockOut of stockOut of stockOut of stock
- Out of Stock
ORION 2.4 Non-Linear Junction Detector
- $21,600
- Read More
-
-
iProtect 1217 Multi-Channel Wireless Detector – TSCM Detection Kit
- $3,350
- Rated 4.00 out of 5
- Purchase Now
-
DD1216 3-Band RF Detector – TSCM Bug Sweep
- $935
- Rated 5.00 out of 5
- Purchase Now
-
Wega Hidden Camera Detector – TSCM Detection Kit
- $595
- Rated 5.00 out of 5
- Purchase Now
-
Hybrid Bug Detector 04 – TSCM Detection Kit
- $2,095
- Rated 4.50 out of 5
- Purchase Now
Portable Tactical Detection Kits are created to detect the various kinds of threats like spying & illegal surveillance devices and illegal wireless signal as we mentioned above.
These items are designed to empower the secure environment by eliminating the feeling of being targeted by the unknown parties & unauthorized surveillance devices.
We are facing with challenge of current innovation, even though innovation is the crucial force to drive our well-being but it also comes with the countless new techniques of privacy invading like threats from wireless networks and covert/hidden surveillance & spying devices that we never realized or never noticed.
Our challenge is to tackle all the potential threats by offering the simplest solutions with the breakthrough outcome to our worldwide clients to modify their own effective countermeasure tactics to monopolize the advantages and create a secure environment for themselves.
The small form of this device allows it to be used for all types of security threat assessments, quick covert assessment, and outdoor assessment effectively.
If you have any questions about technical support & additional product’s specification, you can read our Tactical Detection FAQ, we have provided all useful information and technical support to assist your needs.
We recommend you to read our FAQ before making a purchase.
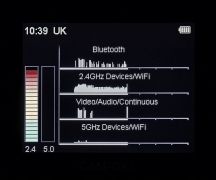
As you can see from the demonstration, Astro i4 has performed to find the unauthorized hidden devices while they are transmitting.
This item is designed to detect the unauthorized hidden devices and harmful signal that harming your privacy.
This item is ideal for portable detection. You can use it anytime when you feel that the environment around you is insecure.
You will not be targeted by unauthorized surveillance devices once you perform the detection regularly.
Benefits of using Detection Kits
1. Fast and precise detection
2. Detects every kinds of modern bugs even in the blind spot
3.You have full authority to control your privacy with the simplest way
4. Lifetime detection tools
5. Locate the actual location of hidden devices and illegal signal transmitter.
6. Able to detect the invisible threats like radio frequency and radio transmission
7. Detects the wireless signal threats ( Hybrid 04 Threat Detector – TSCM Pro Grade )
8. Knows the accurate frequency used by the attackers with the function of Event logging ( Hybrid 04 Threat Detector – TSCM Pro Grade )
9. Once you know the actual frequencies used by the attackers, you can formulate your wireless network countermeasures plan to tackle the problems.
10. Eliminates the insecure conditions of being targeted, tracked and monitored by the unknown parties.